Solid PODs System Map
Sociotechnical Analysis
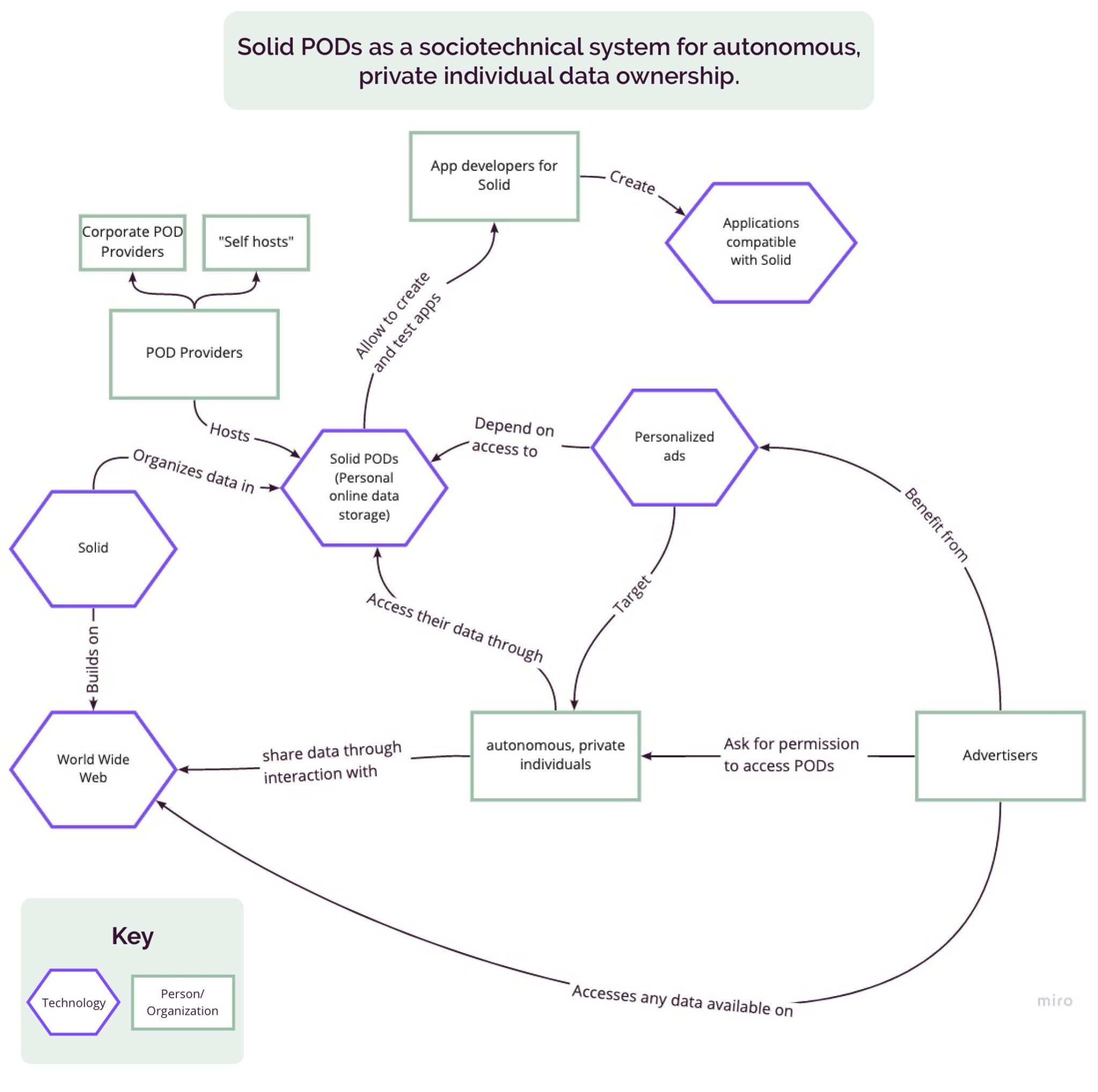
Solid PODs (Personal Online Data storage) as a sociotechnical system for autonomous, private individual data ownership.
The fundamental function of the pods is to store the data of private, autonomous individuals. This is an alternative to the current way that data management, ownership, and storage exists in the World Wide Web. Solid PODs provide users with the ability to grant or revoke access to their personal data for app usage. Without the PODs (i.e. the current state of the World Wide Web), advertisers can access any personal data made available through general user engagement data within apps. However, through POD use, advertisers must request permission from private individuals to access and utilize their data. As advertisers benefit from personalized ads that target specific users based on their engagement with information, the POD system acts as a protective measure for users to control their data. With this new data permission infrastructure, developers that want to make their apps available to Solid POD users must create apps that are compatible with the system. Currently, developers must create their apps under the assumption that the app must store, manage, and utilize data to perform their primary function. However, with PODs, data storage and management is handled by the user themself, limiting any opportunity of exploitation of their personal information. Solid PODs can be self-hosted or hosted by corporate POD providers. Users may elect to self-host due to concerns over corporate POD providers potentially misusing their data as corporate POD providers have their own terms of services separate from Solid. Selection of a POD provider should include a rigorous assessment of individual data needs, third-party involvement, and geographical location of servers.
Data Flow of World Wide Web Versus Solid
To outline the differences between data flows in the World Wide Web and Solid, data permission and access defines the interaction between private individuals, apps, and app developers. For example, in the World Wide Web (see Figure 1b), autonomous, private individuals provide their data through interaction on a social media app. The social media app is then responsible for managing and storing the user’s data in order to leverage the information for its primary function. Applications such as Facebook are then tasked with data access, storage, and management. This provides Facebook with the opportunity to further monetize the data through targeted, personalized advertisements. As the data is stored in a centralized server managed by the application, private individuals have little to no control over how their data is being used once accessed. On the other hand, in the Solid environment (see Figure 1c), when individuals interact with Solid-compatible applications, they are more empowered to manage access to their data. Therefore, when a Solid-compatible application wishes to use an individual’s data, they must first request access to the individual’s identity profile through a Solid POD. Individuals can grant and revoke access to any sliver of information that exists within their POD. Stored data can range from basic files and personal information to more complex data structures. Therefore, through this decentralized data system, POD servers act as a protective measure for apps to use individuals’ data.
Conclusion
One may ask why data access, management and ownership is integral to web engagement? First, companies across the globe have amassed mounds of data from user interactions with their technologies with little oversight and accountability. Due to this predominantly corporate and private centralization of data, individuals’ data may be compromised at any given point. As of May 7, 2021, there is no comprehensive federal privacy law in the United States. Though patchwork, sector-specific legislation are forming, PODs offer an opportunity to address data privacy concerns in individuals’ everyday interactions within the internet. According to John Bruce, CEO of Inrupt (the parent company of Solid), there are three main constituencies on the Web:
- Users want more choice and privacy
- Organizations want more focus and freedom to operate
- Developers want to create exciting data-independent applications
Solid aims to simultaneously address all of these needs without interrupting the current app development process. By relying on existing web standards, Solid acts as a mid-course correction and intermediary that is able to decentralize data collection by growing tech powers. Providing users with Solid PODs grants a level of autonomy that does not threaten their existing desires and usage of web applications. This combats the potential monetization of user data, which plays a role in modern disenfranchisement. Rather, users and organizations experience more transparency and freedom to engage with each other as sought. Organizations and developers are able to focus on the primary functions of their applications, while users have more control over their information and gain insight into data flow and management.
Tetrad of Technological Effects
Using Marshall McLuhan’s tetrad of media effects, we explore what Solid enhances, reverses, retrieves, and obsolesces.
Solid Enhances
By: Mary Margaret Herring
Solid enhances individual data ownership by decentralizing data storage. In the Solid ecosystem, all of a user’s data is stored in a Pod. Because users store their own data - and not companies - users are able to revoke access to that data at any time. This reorientation of the web amplifies user control over data access. The application development process is also enhanced because developers are able to focus on the user facing experience rather than data management. By reading and writing data in users’ Pods, developers are able to obtain and alter the data they need without having to store it.
Solid Reverses
By: Camille Alejandro
Solid reverses how many entities have access to use individuals' data without their prior consent and knowledge. In the internet’s current state, individuals provide data to applications through their app usage, and applications have primary control and ownership over these individuals’ data. Applications are responsible for providing their primary function in addition to data management for users. Using Solid, private individuals store their data in PODs separately from applications. Individuals must manage access requests to their data. However, this responsibility may not be what people are interested in having, so one unintended consequence is giving unwanted burdens to private individuals.
Solid Retrieves
By: Grant Lattanzi
In the current WWW ecosystem, control of access to a person's data doesn't belong to that person, but rather to the providers of different web-based services that person uses. (This is sometimes referred to through the metaphor of a "walled garden," where each website or web-provider stores data in their own walled garden with huge barriers to accessing data from other services.) Solid retrieves this sort of control for the user, and affords them more agency in determining who can access their information. By retrieving control, Solid addresses swathes of privacy concerns that have been growing in tandem with the centralization of the Web. Also, retrieving this sort of access means that the user has increased access to their own data -- they can see and manipulate their data however they would like, as opposed to abiding by the limited affordances of whatever institutions store that data.
Solid Obsolesces
By: Meera Kolluri
Solid PODs offer a functionality in the data storage process that reimagines data rights. Any form of data can be stored in a POD, which creates a new form of storage and permission sequence for data access. With the use of PODs, the owner of the data can grant or revoke access to any portion of their information at any frequency. This allows individuals who engage with the WWW to have access to data storage and processing options that grant them higher levels of data security. As data management is returned to the owner, exploitation, extended retention and unapproved dissemination of data can be reduced.